Home WiFi: If you use a home WiFi network, the basic rules that you should definitely follow are the following:
- Select the highest possible network encryption (usually WPA2). If you’re planning on using WiFi alone or with your family, we recommend taking two more steps – turning on MAC address filtering, which allows you to connect not only to specific devices (you can add more manually) and hide your SSID, i.e. your network’s name. By doing so, it’ll be considerably harder for an attacker to make it onto your network. Select a network password according to safe password rules and change it from time to time.
- Change the login name and password of your router. This is very important – a large number of manufacturers leaves certain pre-installed sets of login data, and if you don’t change them, even the best security becomes completely worthless.
- Some routers can be updated – this means that if you change your network password once every quarter year, you should try find whether there are some updates for your router. A well-secured router is crucial.
The following is connected to this – if you’re out and about somewhere, remember that all communication is public on an unsecured WiFi network. On a coded network, only the administrator can track communication, but that’s not much better. If you do connect to public WiFi, use a VPN – this will make it considerably harder for a potential attacker. You can acquire a VPN either as an addition to your browser or as a stand-alone application. In a free version, you’ll often run into a data limit, but if you’re not downloading films in the café, you should have a comfortable amount of data.
Use an antivirus – it’s definitely worth using some kind of antivirus tool; a classic antivirus program and a firewall are crucial. Both are offered in the basic version of Windows, or you can use the free tools from Avast or AVG.
Use a password manager – this is a very useful tool that will help you minimize damage during a potential breach or theft of your password. You can use various browser extensions or stand-alone applications. These tools generally offer relatively long, technically strong and unbreakable passwords, which are definitely handy.
Update – this is one of the most important rules. If you leave system or application updates for later because it’s not convenient, the chances that it will come back to haunt you are high. This is connected to another piece of advice – don’t use Flash. For example, Flash will work in Chrome only until the end of the year, but try to avoid it if you can.

Screenshot nastavení aktualizace softwaru a oprávnění aplikací na telefonu. Zdroj: Android. Autor screenshotu: KISK.
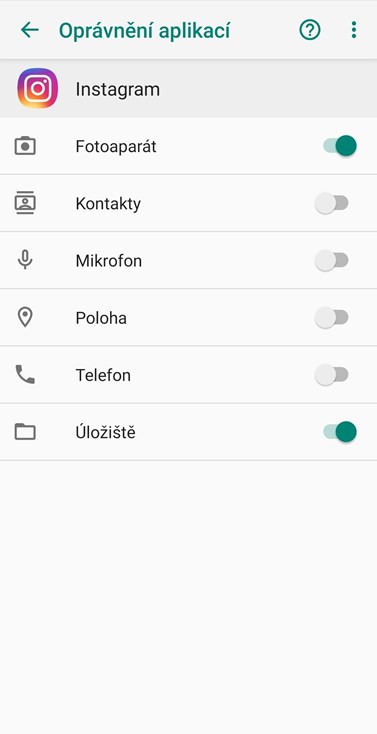
Track authorizations – if you install an application on your mobile telephone, always follow what authorizations the given tool is asking for. Does a flashlight really need access to your contacts or the possibility to make calls? Don’t be afraid to limit your tools even after installing them.
Back things up – a topic that is underestimated (roughly two thirds of all Czechs don’t make backups at all) and important. It’s good to make backups to at least two individual spaces. If you want to make things easier, use tools like OneDrive or Google Drive, which carry out automatic backups, for the most important and irreplaceable things. You should also encrypt things that are secret.
Use your head – many security risks are linked to the human factor. Try not to click on email attachments that look suspicious or are from people you don’t know. Check to see if people aren’t hunting for you via phishing. It’s good to follow current trends and security threats, even though it will take up a bit of your time.
Secure your computer – paradoxically, we sometimes forget about our own system password. You should pay proper attention to it, because if it’s guessed, it usually means that everyone can gain access. Fingerprint readers work well, and are quick and convenient. Whenever you leave your computer, we recommend locking the system (WinK + L).
It’s true that none of these rules above will ensure full security of your device, but it can significantly help. If you want to work even more responsibly with data and your devices, you can also use other tools – safe operating systems, two-phase authentication, hardware keys, etc. The fact is that every small step in security generates a large improvement in your situation and heightens the chances that you’ll avoid an attack or that the attacker will choose a different target.