If we take a look at how people select their passwords, we can track down four general tendencies that aren’t exactly fortunate. The first is the spatial organization of symbols on the keyboard. For example, the twentieth most common password is “!@#$%^&*” or the ninth, “qwerty”, might seem secure at first glance, but only up to the moment when you realize that these symbols run in a sequence on the keyboard. All the aforementioned numerical passwords above belong to this category as well. But look out – even much more educated users who wouldn’t choose such a weak password set up similar ones while unlocking their telephone via a gesture like swiping. Please don’t do this – these are the easiest passwords to guess, and what’s more, they’re easy to see on a mobile phone and your finger will leave smears where your password was entered.
The second group of bad passwords are those which we could call “dictionary” passwords – this includes the word “password”, password123, or “iloveyou”, which came in at number ten in the ranking. If you want to try to guess a password, dictionary methods are some of the quickest and most successful.
The third group of passwords are those that have been generated by a service or administrator, but are so complex that a user can’t remember them. The user writes them down on a sticky note next to their monitor or stuffs them into a wallet or somewhere else. Passwords on sticky notes are a bad habit, and aren’t useful at all. Get rid of them while there’s still time. These passwords most commonly appear as login passwords for work or school computer networks.
The last method for bad passwords is linking them to something that is in your close vicinity – “Max” or “Natalie” aren’t great ideas for passwords if your dog’s name is Max and your good friend’s name is Natalie, because a person who will often want to guess your password is someone very near you, and these are things they’ll be able to guess fairly easily.
So how should we select a good password? Generally speaking, it should be a combination of capital and lowercase letters, numbers and special symbols, ideally in a way that you can remember. For example, the password “19Kdmkdmvhplbsps18” is quite a nice password that follows the first letters of the beginning of the Czech national anthem and the year 1918. The first letters in a poem or song can be a good starting point. The longer the password the better, but it usually doesn’t have to be as long as the one above – you can get by with six to nine symbols – “19Kdmkdm?”. Someone will have an extremely hard time guessing one like that too.
If you can, try to use a password manager – with one, it’s enough to remember one or two strong passwords, and the system will generate relatively long and basically unhackable passwords for individual services. In Chrome, for example, we can recommend LastPass or Password App, but the selection is significantly broader.
It’s definitely necessary to carry out regular password checks, and two useful services can do this. If you’re using Chrome (like around 70% of users), it offers a Password Manager with the possibility of checking the passwords that are saved in the browser (which almost everyone does – this is, however, dangerous if you leave your computer and don’t log out).
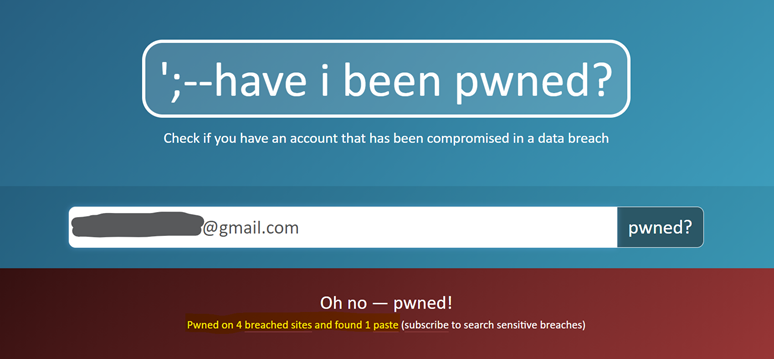
Ukázka z webu Have I Been Pwned, který zjistil, že ze zadaného emailu uniklo heslo. Zdroj: Have I Been Pwned. Autor screenshotu: KISK.
Definitely try out Have I Been Pwned. You give your email to this service and it checks if it is in publicly available datasets of password leaks. If it is, it means that your password is known or threatened and you have to change it. The service naturally doesn’t know if you have the same password for all services or just one, so you have to take relevant action or a set of actions. These public datasets are easily accessible, and if someone wanted to guess your password, they’d look there first. The service allows you to set up notifications if your email appears in such a breach.
To conclude, here are two more recommendations. Primarily, it’s said that you should have a unique password for each service. If you’re not using a password manager and you don’t have a perfect memory, such an approach is impossible. Try at least to differentiate between unimportant passwords, which can be fairly similar everywhere (for example on e-shops or similar services), and valuable ones, and pay sufficient attention to them (for example your social networks or email account). Secondly – use two-phase identification if possible (i.e. a combination of a password and a code sent via text message to your mobile phone or via an app notification). It’s not the most convenient method, but the chances it will be hacked are very small.
